SARK V4.0.0 Firewall
Firewall
For Debian based SARK Appliances (S200 & S500) and vanilla Debian SARK builds, SARK has the Shorewall Firewall on-board and provides a simple GUI to control it
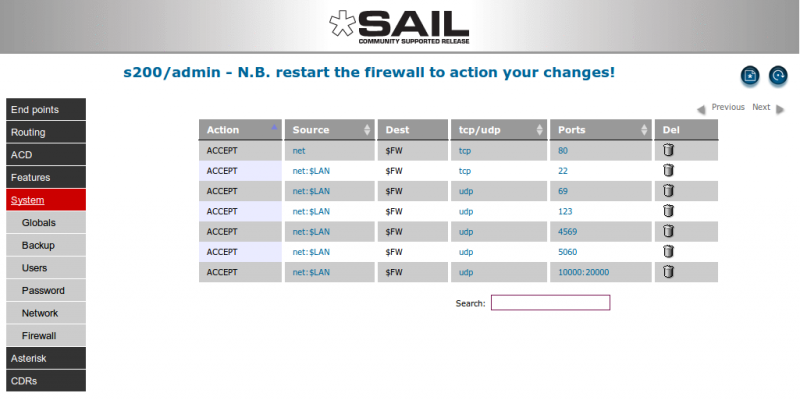
By default the firewall is set as follows:
- allow HTTP port 80 from anywhere
- allow SSH port 22 from the local lan
- allow TFTP port 69 from the local lan
- allow NTP port 123 from the local lan
- allow IAX2 port 4569 from the local lan
- allow SIP port 5060 from the local lan
- allow RTP ports 10000-20000 from the local lan
Everything else is denied.
Setting and changing rules
SARK supports a simple subset of the shorewall ruleset, however it is enough to be able to who will be allowed into the system. You only need specify 3 variables to create a rule; Source, Protocol and Destination Port.
The Source column
The SOURCE column decides who is allowed in (i.e. from where). There are 2 keywords; net and $LAN and you specify addresses and ranges in CIDR format. The SOURCE rule always begins with net. If you put nothing else then you will open a port to the entire internet. Port 80 is initially defined in that way.
You can be more sepcific by specifying net followed by a colon (:) then by an address range (in CIDR notation). You can also use the special variable $LAN to restrict access from the local lan ONLY. Lets say we want to allow access from IP address 81.43.44.9; we could put
net:81.43.44.9
Or, to allow a subnet-range we might put something like
net:81.43.44.0/29
To restrict access only from our local lan we can put
net:$LAN